The Access Management Challenges
Policy Model Complexity: Managing
access policies becomes increasingly complex when dealing with
diverse policy models across multiple users or tenants. Each
user or tenant may have unique requirements, leading to a
proliferation of policy rules and conditions that must be
managed and enforced.
Data Model & UI: The data model
and user interface (UI) in access management presents a
challenge, particularly in Attribute-Based Access Control (ABAC)
environments where the data model varies by use case. For
example, payment authorization may involve a data model of
account numbers and maximum amounts, while user management may
focus on departmental access. These differing models require
unique UIs, making it difficult to create a generic access
system.
Data Redaction: Data redaction in
large datasets, particularly in paginated environments, presents
significant challenges. The process of determining whether each
list item should be returned one by one can result in
performance issues, making it difficult to efficiently redact
sensitive information while maintaining acceptable system
performance.
Attribute Retrieving:
Integrating external data sources to support access
decision-making presents a significant challenge, particularly
when dealing with diverse types of data stores and the need for
efficient data loading and caching mechanisms. The process
involves accessing and retrieving data from various external
sources, such as databases, APIs, or third-party services, and
incorporating it into the access management system to inform
access decisions in real-time.
Regulatory Compliance:
Meeting regulatory requirements, such as GDPR, HIPAA, PCI DSS,
and SOC 2, imposes challenges related to data privacy,
auditability, consent management, and data protection across
multiple jurisdictions.
Change Management:
Managing changes to access policies, user roles, entitlements,
and permissions over time while ensuring consistency, accuracy,
and compliance requires robust change management processes and
version control mechanisms.
Auditability and Reporting:
Providing comprehensive audit trails, logging, and reporting
capabilities to track access activities, monitor policy
violations, and demonstrate compliance with regulatory
requirements is essential but challenging to implement
effectively.
The Answers to the Challenges
Clear Entitlement effectively addresses the challenge of policy complexity by introducing a robust and flexible policy engine built upon the foundation of XACML while extending its capabilities beyond traditional models. By leveraging a model that encompasses Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), Clear Entitlement offers organizations the versatility to define and manage access policies tailored to their specific needs.
Clear Entitlement offers robust support for both fine-grained data entitlement and functional entitlement. Data entitlement safeguards the system by controlling access to specific data resources at the API level, ensuring only authorized users can access them. Meanwhile, functional entitlement enhances user experience by dynamically adjusting the UI based on user access rights. For example, developers can customize the UI to show or hide menu items dynamically according to the user's permissions. Clear Entitlement further streamlines this process by providing a bulk API to retrieve functional entitlement for all nodes within a branch of the resource tree. This capability allows for efficient and precise control and customization of UI components.
Clear Entitlement establishes its provisioning model atop SCIM, facilitating customizable SCIM extensions using JSON schema to accommodate various entitlement models. This approach enables organizations to define custom attributes such as authorized accounts and maximum payment amounts within the SCIM schema. Beyond policy management, Clear Entitlement empowers users with intuitive UI features for managing SCIM data and extensions. Customers can seamlessly modify the UI schema to tailor the data model according to their specific requirements, allowing for effortless customization and adherence to US customization standards
To address performance challenges associated with data redaction and pagination, Clear Entitlement adopts a sophisticated security filter approach, optimizing the retrieval of authorized data while minimizing processing overhead. Unlike traditional methods that involve checking access individually for each search result, particularly cumbersome with large datasets and pagination, Clear Entitlement efficiently returns only authorized data using security filters. Customers benefit from the flexibility of defining templates within policy obligations to generate filters tailored to different data stores, such as SQL, NoSQL, LDAP, and more. Alternatively, customers can choose to return JSON obligations to the Policy Enforcement Point (PEP), which translates them into filter objects, such as Hibernate detached criteria or prepared SQL statements. This facilitates seamless integration and efficient data retrieval.
Clear Entitlement provides a robust solution for policy change management through its out-of-the-box (OOTB) workflow capabilities. This feature streamlines the process by defining three distinct roles: Policy Modeler, Policy Approver, and Policy Deployer. Each role is assigned specific responsibilities to manage the lifecycle of policies effectively. The Policy Modeler is responsible for creating and modifying policies, while the Policy Approver ensures the accuracy and compliance of proposed changes. Finally, the Policy Deployer oversees the deployment of approved policies into production environments. Additionally, Clear Entitlement supports policy export and import functionalities, enabling seamless promotion of policies from lower environments to production. This feature ensures consistency and reliability across different environments while facilitating efficient policy management and deployment processes.
Clear Entitlement offers comprehensive support for Segregation
of Duties (SoD) with two distinct options tailored to meet
varying organizational needs. The first option,
Mutually-Exclusive Roles, allows organizations to define roles
that are mutually exclusive, ensuring that individuals cannot
simultaneously hold conflicting roles. Clear Entitlement
generates violation reports to identify any instances of role
conflicts, enabling organizations to promptly address and
rectify violations.
Alternatively, Clear Entitlement provides dynamic SoD policies
for scenarios where the static nature of mutually exclusive
roles is not suitable. For example, an organization may permit
individuals to serve as both a maker and a checker, as long as
they do not act on the same transaction. In such cases, Clear
Entitlement facilitates the implementation of policies that deny
access if a user is already involved in a transaction, thereby
preventing potential conflicts of interest. This dynamic
approach to SoD policy enforcement ensures greater flexibility
and adaptability to complex organizational structures and
requirements, ultimately enhancing security and compliance
measures.
Clear Entitlement integrates cutting-edge artificial intelligence (AI) capabilities to enhance its access management functionalities. By meticulously logging both policy management and runtime access auditing records, Clear Entitlement accumulates a wealth of data ripe for AI analysis. Leveraging AI algorithms, Clear Entitlement performs Anomaly Detection to identify unusual access patterns or behaviors that may indicate potential security threats or policy violations. Furthermore, the system conducts Access Review and Remediation processes, scrutinizing access rights and usage patterns to ensure compliance and mitigate risks. In addition, Clear Entitlement employs Role Mining techniques during user re-certification exercises, analyzing access patterns to identify and refine role assignments for optimal access control. With its AI-driven features, Clear Entitlement empowers organizations to proactively detect anomalies, maintain compliance, and optimize access management processes.
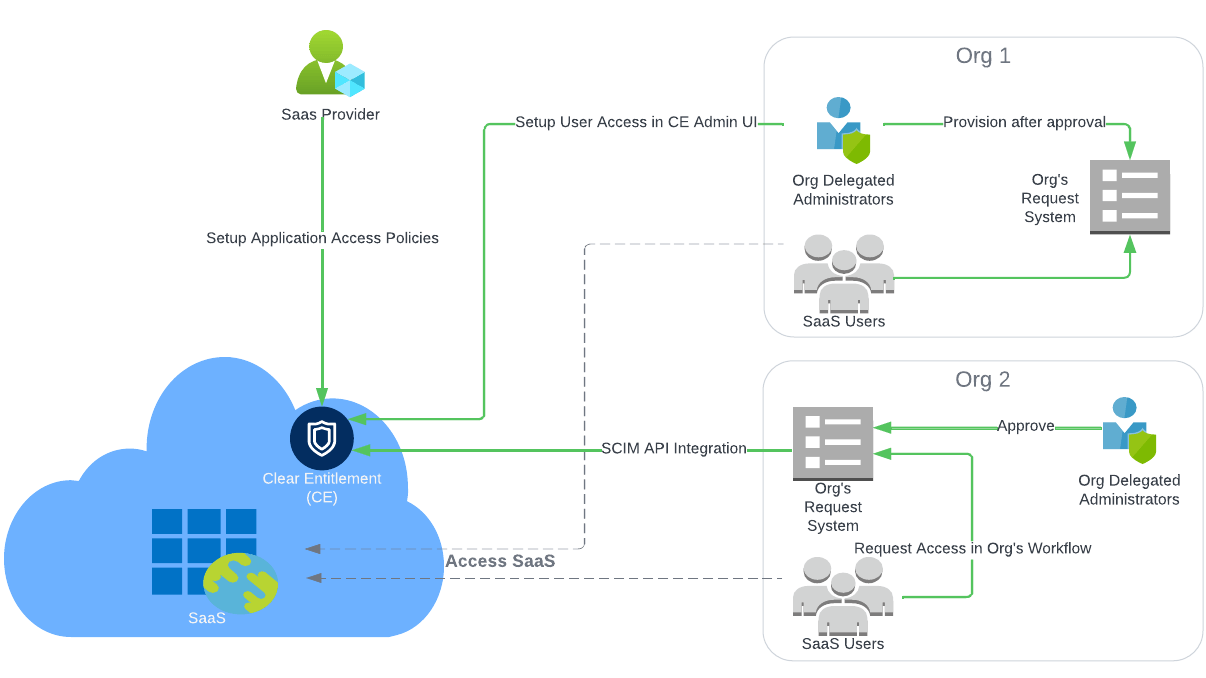
Provisioning
Clear Entitlement supports two provisioning models:
Option 1 : Utilize Clear
Entitlement's internal data store. With this option, customers
leverage their existing request workflow, enabling users to
submit access requests through established channels. Upon
approval, access can be provisioned either manually by
organizational administrators through the SCIM UI or
automatically via SCIM API integration into Clear Entitlement.
Clear Entitlement offers comprehensive support for various data
entities, including user, group, role, entitlement, user-group
membership, user-role membership, user-entitlement membership,
group-role membership, role-entitlement membership, user
attribute, group attribute, role attribute, entitlement
attribute, user-role membership attribute, and group-role
membership attribute. These entities are readily available and
can be easily loaded using built-in attribute retrievers for
efficient policy evaluation.
Option 2 : Utilize the customer's data store. In this scenario, customers can provision data into their own data store, such as Active Directory or an application database. This approach offers flexibility while maintaining strict access controls, allowing organizations to tailor their access management processes to their specific requirements and infrastructure setup. Keeping entitlement data in the application database is particularly beneficial when data redaction involves a large amount of entitlements. Customers can use out-of-the-box attribute retrievers to fetch data from external data stores like LDAP for policy evaluation, or create customized attribute retrievers.